Over $26 billion had been lost from June 2016 to July 2019 internationally and in the United States.
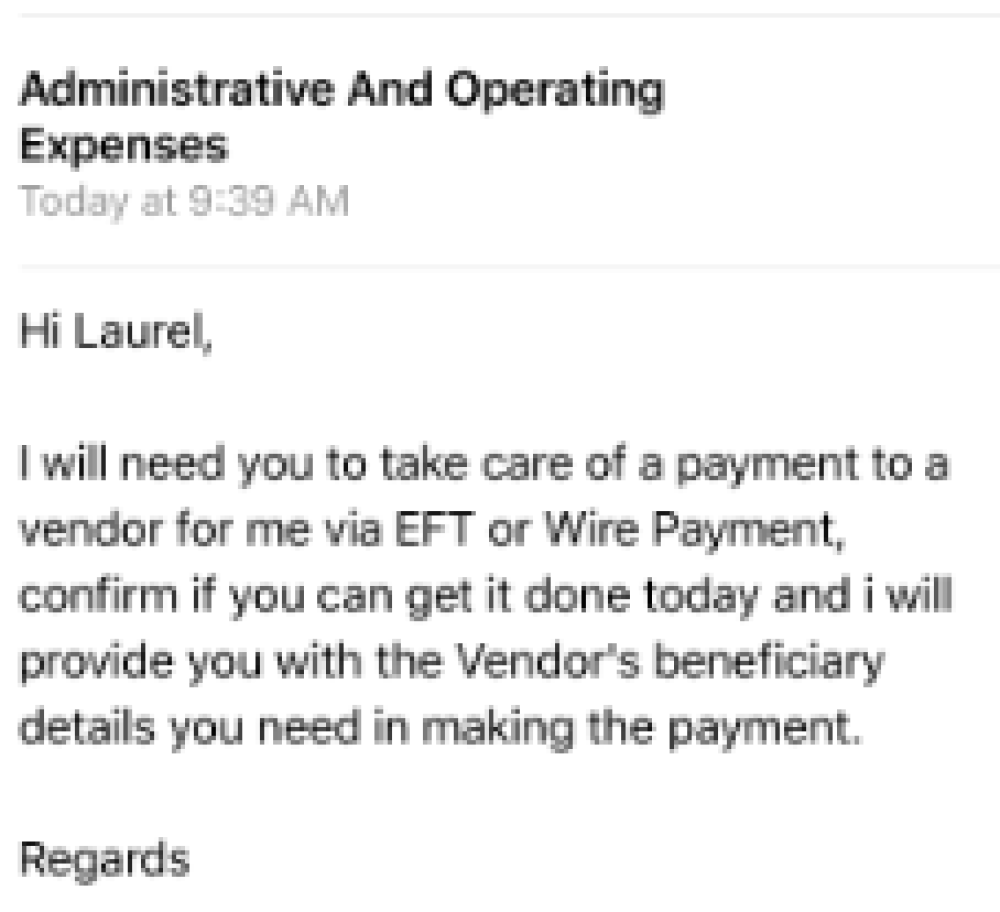
This week we are going to shine the light on email account compromise (EAC) and resulting fraud losses. It’s also been called the “business email compromise (BEC)” or the “CEO wire scam”, but it happens just as frequently to personal email accounts. Non-profit organizations are increasingly reported as targets as well. Consider this scenario: you receive an email from the Executive Director of the non-profit you volunteer for, asking you to buy gift cards for an upcoming fundraiser. You run out to the local CVS or Walgreens and diligently purchase the iTunes gift cards and promptly provide the codes on the back of the card so that your non-profit can continue on with its good work. Problem is, it wasn’t really your Executive Director, and now you are personally out the money!
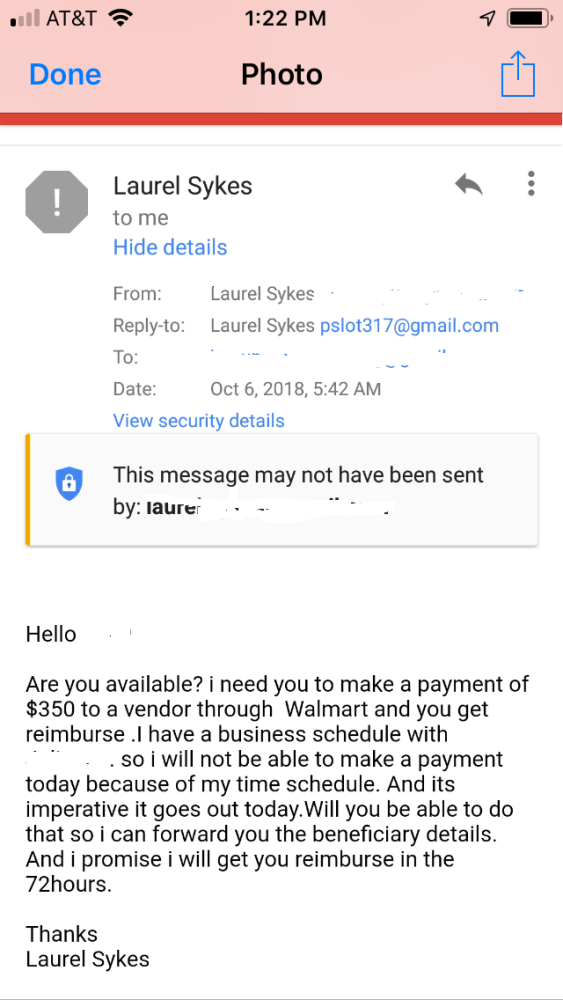
The Federal Trade Commission reported last year that 26 percent of people who report being scammed in 2018 said they bought or reloaded a gift card to deliver the money, up from 7 percent in 2015. The FTC said that gift card-related losses reported to the agency totaled $20 million in 2015, $27 million in 2016, $40 million in 2017, and $53 million in the first nine months of 2018 alone. Scams often originate first through email "spoofing", when someone sends an email with a forged sender address. Typically, the sender’s name or email address and the body of the message are changed to mimic a legitimate source such as a bank or a company you do business with. They can also mimic messages from friends and family.
The FBI also issues regular reports on email compromise scams based upon reports filed through their online site at www.ic3.gov. The bulk of their reports focus on business transactions, such as cases where a CFO or controller of a business have fallen prey to wiring money out to a fraudster believing their CEO had sent them an email asking them to do so. In prior years scams highlighted by the FBI heavily targeted the real estate sector in recent years. This would include title companies, law firms, real estate agents, buyers and sellers, where a spoofed e-mail has been sent or received purporting to be one of the parties involved in the real estate deal with instructions directing the recipient of the email to change the payment type and/or payment location to a fraudulent account.
The FBI issued a public service announcement just last month reporting over $26 billion had been lost from June 2016 to July 2019 internationally and in the United States as reported through their online channel at www.ic3.gov. While the FBI cites the increase is due (in part) to increased awareness to report the fraud there are countless cases every day that go unreported. According to the FBI, the BEC/EAC scam continues to grow and evolve, targeting small, medium, and large business and personal transactions. Many of the cases reported to the FBI through ic3 involve requests for wire transfers, and banks located in China and Hong Kong remain the primary destinations of fraudulent funds. However, the Federal Bureau of Investigation has seen an increase of fraudulent transfers sent to the United Kingdom, Mexico, and Turkey. Personally, we might see an email or text we believe to be from a friend or colleague asking for money, or to buy iTunes or Google Play or other gift cards.
According to the most recent PSA https://www.ic3.gov/media/2019/190910.aspx, the FBI has received an increased number of BEC complaints concerning payroll, where the human resources or payroll department receives spoofed emails appearing to be from employees requesting a change to their direct deposit account. Alternatively, the fraudster gains access to an employee’s direct deposit account and alters the routing to another account.
The FBI cautions that the scam is not always associated with a transfer-of-funds request. One variation involves compromising legitimate business email accounts and requesting employees’ Personally Identifiable Information (PII) or Wage and Tax Statement (W-2) forms. That data can later be used in another common scam where the fraudster files taxes on the victim’s behalf to obtain the tax refund!
Some companies report receiving “phishing” emails prior to receiving requests for changes to direct deposit accounts. In these cases, multiple employees may receive the same email that contains a spoofed log-in page. Employees enter their usernames and passwords on the spoofed log-in page, allowing the fraudster to gather and use employee credentials to access the employees’ personal information.
Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.
Below are some tips from ARB and the FBI for preventing losses through these scams. Pass the information along to your friends and colleagues – spread the word! Our own President and CEO, Jeff Devine, leads the way by periodically sending out bankwide communications reminding employees not to fall prey to CEO scams:
“…In some cases, the scammer asks the employee to buy online gift cards and supply the gift card info, or maybe asks someone in HR to make a payroll change (like changing an employee’s pay from their real bank account to an account the scammer controls.) Please know I’m not going to ask you to send a wire transfer or do an ACH by email or text. I’m not going to reach out to you outside business hours with unusual requests involving account changes or moving money around. When in doubt, just stop and call!”
Jeff DeVine, President & CEO at American Riviera Bank
Other helpful tips:
Thanks for reading, and stay alert!
Previous: Social Engineering Next: Start the New Year Off Better